Introduction
This article outlines a uniform method for retrieving certificates from the Windows Certificate Store. For those less familiar with certificates and the store itself, here’s a quick overview:
A certificate is tied to an entity, such as a web server, and is typically used to prove identity (authentication), encrypt data, or validate the origin of a message (signatures). Certificates include a public key and, optionally, a trust chain (comprising intermediate CAs and root CAs). In Windows environments, a common location for managing certificates is the Windows Certificate Store. For a deeper understanding, visit Microsoft Documentation for Certificates.
The Challenge
In practice, different applications select certificates from the Windows Certificate Store in inconsistent ways.
Example:
Both Application A and Application B allow specifying an alias (e.g., "localhost") to identify a certificate.
- Application A searches by subject name
- Application B searches by friendly name
If both are configured with the alias "localhost," Application A might successfully find a certificate, while Application B fails.
→ See Image 1 for a sample certificate where the subject name and friendly name differ, illustrating the mismatch between Applications A and B.
In such a scenario, the alias would need to be set to ‘my-friendly-name’ for Application B, thus causing a deviation in both configurations.
Initial workaround: Using a certificate's hash value.
While this ensures exact matches, it breaks when certificates are rotated, as the hash changes. Therefore, a better solution is needed: one that allows the use of an alias to identify the correct certificate—even after rotation consistently.
Why Standardization Matters
In environments with multiple software product lines, inconsistencies in certificate selection can lead to support overhead, troubleshooting complexity, and rollout issues. A unified approach is essential.
To address this challenge, a standardized procedure for selecting certificates by alias was defined. This procedure was implemented in both Java and C# as the Windows Certificate Selection Library (WCSL).
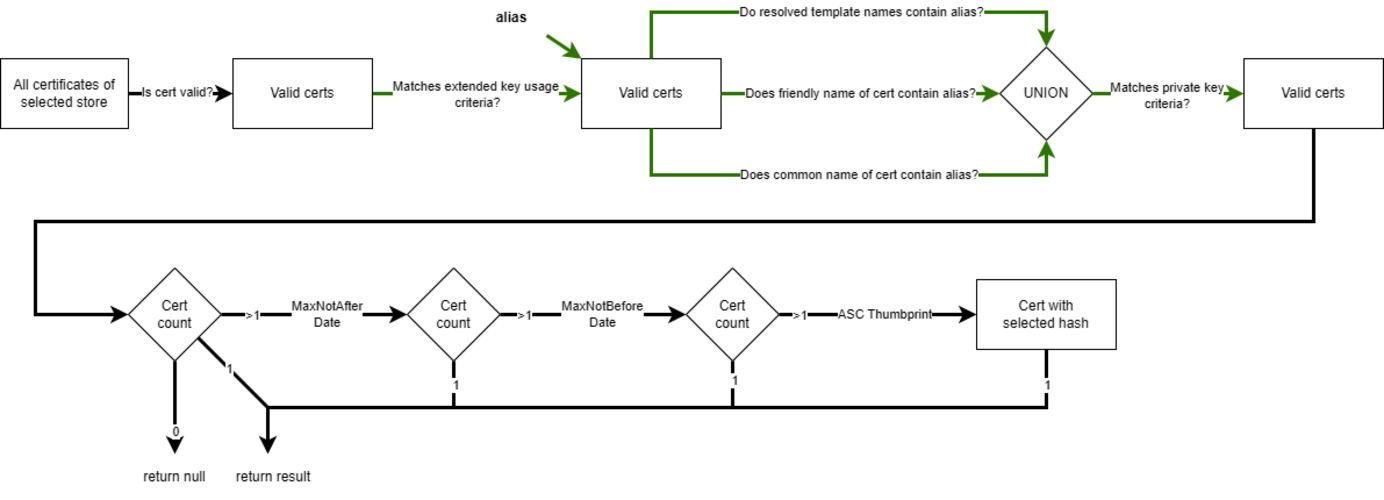
To standardize the selection of certificates across applications, the Windows Certificate Selection Library (WCSL) defines a step-by-step procedure that is both configurable and deterministic.
→ See Figure 1 for a visual representation of the WCSL filtering and selection stages.
WCSL starts by listing all certificates for the specified store. Supported stores include Windows-My and Windows-Root. Once listed, the filtering process begins:
- Expired certificates are excluded.
Only certificates that are valid at the current UTC time are considered. - Certificates without the required Extended Key Usage are filtered out.
This step rejects certificates that do not match the selected Extended Key Usage (see RFC 5280 (Extended Key Usage). Typical filters include SERVER_AUTH and CLIENT_AUTH. It is also possible to skip this step entirely. - Alias containment is checked against several certificate properties:
- Friendly Name – a custom name within the Windows Certificate Store (Microsoft Docs – X509Certificate2.FriendlyName)
- Template Name – the resolved name of the certificate template used during creation.
- Subject Name – including DNS names in the Subject Alternative Name (SAN) extension (RFC 5280 (Subject Alternative Name)) or the Common Name (RFC 5280 (Issuer)) – see article “What is a Multi-Domain (SAN) Certificate?” for reference.
The alias serves as the input for this matching process. This behavior is configurable. For example, matching may be based on template and subject name or restricted to the friendly name only.
4. An optional step checks for the existence and accessibility of a private key.
When enabled, only certificates with a loadable private key are considered. When disabled, certificates without a private key—or those with inaccessible keys due to permission issues—are still included.
After applying the filtering steps, the result is typically zero or one matching certificate. In edge cases where multiple certificates remain, additional deterministic steps are used to ensure selection without ambiguity:
5. The certificate with the latest expiration date is selected.
6. If a tie remains, the certificate with the most recent validity start date is chosen.
7. If multiple certificates still match, the one with the alphanumerically lowest SHA1 hash is selected.
Benefits of Using WCSL
To ensure consistent behavior across all applications, WCSL is used with a standardized configuration for the customizable steps. This approach delivers several key advantages:
- Faster troubleshooting
- Unified certificate logging
- Reduced development time
- Automatic support for certificate rotation
Conclusion
Applications and frameworks tend to handle certificate selection differently. This complexity increases when factoring in varying customer deployment strategies. WCSL addresses this challenge with a configurable, flexible approach for selecting certificates from the Windows Certificate Store.
With implementations available in both Java and C#, the procedure brings consistency, reduces support effort, and enhances maintainability across all products and environments.
Organizations seeking to streamline certificate selection across various systems and frameworks can benefit from adopting WCSL. The library is compatible with Java and C# environments, supporting scalable and maintainable certificate handling.
Would you like to learn more? We are here for you!